Introduction and Delivery:
Full form of RAT : Remote Administration Tool
Full form of Recmos: Remote Control & Surveillance Software
One of the things Remcos is used for is Remote Control. It can be used to fully manage one or more computers from afar. If you want to do this on one or many computers, you can use this to do it. The main package, Remcos RAT, is shown. In the beginning, it was sold as a tool that let people control a computer from afar.
Scientists at Malwarebytes have been watching a unique malspam campaign for the last few months. The campaign uses emails that are about money to send the Remcos remote access trojan (RAT) to people who open them. The majority of the time, Remcos comes in the form of malicious documents or archive files that have scripts or executables inside of them. Remcos, like other RATs, gives the threat actor full control over the computer that has been infected. This means that they can take screenshots, record keystrokes, or get other important information from the computer, as well as other things. It isn’t used by people who are bad. Remcos, on the other hand, isn’t. People who buy Remcos from Breaking Security see it as a way to run their business.
Delivery
They have hidden macros that run shell commands that get and run malware, so they can get and run it. There are a lot of “ghost” characters added to the real text to make it more difficult to read, so it’s not easy to read.
To be able to run the malware with a lot of power, it uses a well-known way to get around UAC. You can try to make it run as part of Microsoft’s Event Viewer by hijacking a registry that it uses to figure out where the Microsoft Management Console is. This registry, HKCUSoftwareClassesmscfileshellopencommand, tells the computer where the Microsoft Management Console is (mmc.exe). If something stands in its way, the Event Viewer runs it, no matter how long it takes. In this case, the macro’s shell command moves a value from that registry entry to the location where the malicious software is stored, so that the malicious software can get it. A virus instead of mmc.exe is run.
There are two version of Recmos RAT available:
First one is free version having limited features.
Second one is premium version. You can get access to every feature.
To get Recmos RAT, Click here.
History, Sample and Diagnosis of Remcos RAT:
Recmos RAT was first seen on 2016 delivered in malicious mail.
After that, the use of Recmos RAT is going beyond the imagination:
The full history of the Recmos RAT can be seen from here.
The sample of Recmos RAT can be seen below:
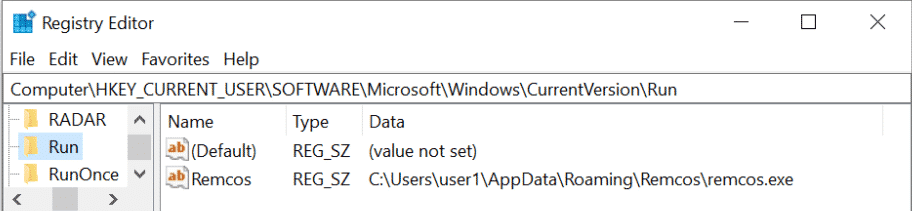
To see if your system is infected or not: Follow the following steps:
1. GOTO Computer.
2.GOTO HKEY_CURRNET_USER
3. GOTO SOFTWARE
4. GOTO Microsoft > Windows
5. GOTO CurrentVersion > Run
If you can see Recmos as above, it means your computer is affected.
(Note: It is not always necessary that only this method can diagnose the infection of the Recmos RAT. It means, you can still be infected without any symptoms of Recmos file in the Registry Editor. So always make sure to diagnose the Recmos RAT by using other methods of diagnosis)
About the Threat :
The first time it was seen in 2016. It has kept getting better ever since. It’s easy to find on the dark web, and it gets new features about once a month.
It was downloaded firstly through the phishing email. In an MS Office file, users are asked to turn on macros when they open it. When Remcos is done infiltrating, he does this. Remcos uses the same techniques that most known malware does to spread.
When someone got a fake email, they were sent a sample XLS file that was used to do some analysis. It ran a virus when this file was opened. They then downloaded the next attack payload, which was very hard to read because the scripts had been changed. Because this payload was also written in a way that was hard to read, It does these important things :
- Download Another Payload
- It automatically move this payload to different location and rename it.
- Can MODIFY to execute the payload during Windows startup.
- Malware Functionality
The types of file that leads to the Attacks are :-
- Quotation.xla
- rthfy.exe
- Quotation.exe
Activities and Capabilities of Recmos RAT:
The following things can be easily done by the Recmos RAT:
- Every time Windows OS is started, it starts up and runs.
- Complete control and command of the infected system remotely.
- The removal of data from a computer that has been infected.
- A lot of the malware itself was made to be hard to read.
- Features that are always changing and getting new updates.
- An anti-debugging feature that hides from detection.
- The ability to record the keystrokes of a computer that has been infected with a computer virus
- Ability to take screenshots of a computer that has been infected.
- The ability to run distribution campaigns with a mass mailer
- DynDNS is a service that connects clients and servers.
- The attacker’s ability to use the infected computer as part of a botnet is also important.
Once the system is hacked, Recmos gives the attacker full control over the computer, including the ability to record keystrokes and take screenshots. This gives the attacker a lot of power. It can send information from a computer that has been hacked to the attacker’s servers.
How to build Remote Access Trojan ( RAT) – For Educational Purpose Only
Before the dive to build Remote Access Trojan, Let’s have a look at some well-known Trojans and Trojan Building Tools. They are:
1.Casa RAT
2.Back Orifice
3.Bandook RAT
4.Dark Comet Rat
5.Cerberus
6.Cybergate
7.Blackshades
8.Poison Ivy
9.Schwarze Sonne RAT
10.Syndrome RAT
11.Team Viewer
12.Y3k RAT
13Snoopy
15.5p00f3r.N$ RAT
16.NetBus
17.SpyNet
18.P. Storrie RAT
19.Turkojan Gold
20.Bifrost
21.Lost Door
22.Beast
23.Shark
24.Sub7
25.Pain RAT
26.xHacker Pro RAT
27.Seed RAT
28.Optix Pro RAT
29.Dark Moon
30.NetDevil
31.Deeper RAT
32.MiniMo RAT
I have to tell you that the list isn’t complete and that only 25% of the tools used to build RATs are on it.
How to make a RAT: This is a demonstration.
Because there are so many tools and most of them have the same kind of interface, we can choose any RAT-building tool to show off. So we choose Cerberus Client to show how the RAT works. Please keep in mind that using a RAT to hack into computers is illegal, so please only use this demonstration to learn about it.
When you search on Google, type “Download Cerberus RAT.” Then, download Cerberus RAT. When you open the file called Cerberus, the program will start up. If you agree to the terms of service, the next interface will open up in front of you.
To make a server, click the new button.

As you can see, there are a lot of settings you can choose from. For our demonstration, we’ll use the most common settings. It is in the “Basic Option.” In “Basic Option,” type your IP address and then press “+.” Server identification names are used by your clients to tell which server they are connecting with. This name helps your clients figure out which server they are connecting with. There is no need to say what to put in the connection password. Select the port on which you want to listen. Keep this port in mind because you’ll need to set up your client to get information from this port.
“Server Installation” is the next choice. When you click “Directory Installation,” you can choose where and with what name your RAT server will be installed. When you choose “File Name,” you have to choose the name and extension of your server. Boot Methods gives you the option to start your server as a “System Service” or “User Application.” You can choose which one you want, or leave them the same. Anti-debugging lets your RAT get around Virtualization and Sandboxing.
From “Misc Options,” you can turn on keylogging and choose how your RAT hides in another process. You can also turn on keylogging from this menu.
“Display Message” lets you show a custom message on the computer of the person you’re trying to help.
“Black List Item” lets you set rules for how your RAT server runs when it comes to a specific process or service. It’s mostly used by more advanced users.
“Overview” lets you look at the features of your RAT. Now, choose an icon and click the “create server” button to make a new server.
It’s now possible to link your RAT to any legal file, but most likely it will be a program that you can run to set up your computer. To stay hidden, don’t use a custom message box and don’t check the “Run in Visible Mode” option when making a server.

To configure Cerberus to listen on a certain port, go to Options and enter the “Connection Password” and “Connection Ports” that were selected in Server. Wait for the victim to execute the server, then right-click on the listening server and experiment with the parameters.
The above instruction is solely for educational purposes, and I will not be held liable if you use it for any other reason.
Traces/IOCs:
Files:
.SettingContent.ms
PcHealths.exe
Hashes:
8710e87642371c828453d59c8cc4edfe8906a5e8fdfbf2191137bf1bf22ecf81fc0fa7c20adf0eaf0538cec14e37d52398a08d91ec105f33ea53919e7c70bb5aff64d7dc2f60fd79304639393cf70fed82e3eb1395d9f331ba123bd4e5f75923.exe
Consequences:
Trojan. Remcos lets the person who got the computer infected run keyloggers and surveillance mode (audio and screenshots) on it. Remcos lets the person who got the computer infected run keyloggers and surveillance mode on it.
- Some information about the system may have been stolen, so you should be on the lookout.
- There is a chance that the user’s passwords have been stolen.
- Digital coins may have been stolen, so you should be wary of what you do with them.
- As time goes on, a backdoor could make the system even more at risk for attacks and infections.
Conclusion
A person doesn’t need to be an expert to make malware attacks that aren’t very hard. In this article, we can see that using Recmos is not that difficult. So people who want to do bad things find Remcos more appealing because more apps like Remcos are being made public. As long as you click a few times, you can get one of them, too.
This is how many RAT authors try to stop people from using their tools for bad things. If people report it, they can lose their licenses. As soon as the thin layer of it being an administration tool comes off, it turns out to be a full-blown malware builder. Most of the time, this is just to keep them from being sued.
That was all for this article where we took a look at the Remcos RAT.
More Posts from us:
Android Hacking Setup and SSL Pinning Bypass
How to Install Cobalt Strike on VPS in 2022
How to install Metasploit in Ubuntu Server(VPS)
