Android hacking is fun and less talked about when comparing to hacking websites. Android hacking setup is not easy as Web as it requires lots of setup and time in SSL pinning bypass in android apps. Also very few bug bounty hunter test android apps and there lots of opportunites to be explored in mobile apps bug bounty. In this article, we are going to discuss about setting up our android hacking and few ways to bypass SSL pinning in android apps.
Requirements
- Android Emulator
- Python
Python Setup
Setting up python wouldn’t be difficult. Just go to python.org and download. After downloading click on the setup file, while setting up make sure to Add it to path while doing installation.
We need frida and objection on our system to help with SSL pinning bypass on android apps. Install these from command prompt using following commands. We will talk more about this while using it for SSL pinning bypass.
pip install frida-tools
pip install objection
Noxplayer Setup
We are going to use Noxplayer as emulator for our setup. To download Noxplayer, click here and download Noxplayer for our android pentesting setup.
After succesfully setting up Nox emulator, make sure to enable root option. To do so, click on settings > General > Check root option > Click on save. It will now ask for restart, click on restart.
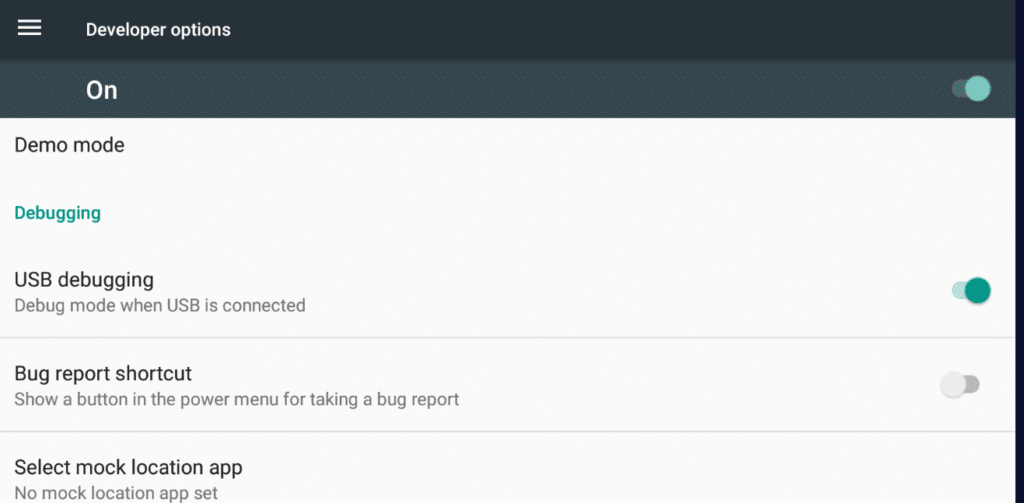
Now we have to enable USB debugging in our android emulator Nox. Follow these steps
- Click on Tools, go to settings and click on About Tablet.
- Scroll down and you will find build number, click 7 times and it will enable developer option.
- Go back to settings home, and you will see developer options at bottom.
- Enable USB debugging option.
- Now go to file location where Noxplayer is installed, it is generally in C:\Program Files\Nox\bin . It may differ according to your system. open command prompt in that folder by entering cmd in file location and it will open a command prompt. Type the following command
nox_adb.exe connect 127.0.0.1:62001
Now we have successfully setup the emulator.
Proxying Android
To to Pentesting on android apps, we need to proxy to analyze request and responses. I am using Burp Suite as proxy.
- Go to Burp Suite, click on Proxy Tab. Add as new port to listen like in the picture.

- Check your local IP using ipconfig command.
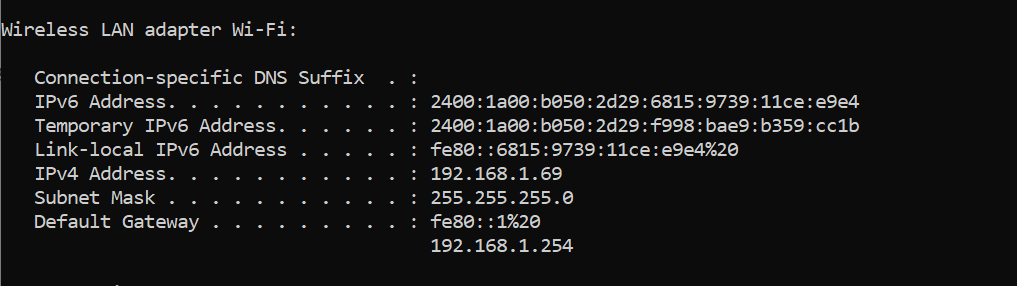
- Now to go Nox Emulator, open WI-FI settings. Long press on wifi, click on Modify Network.
- Click on Advanced options > Proxy > Manual and put your local IP and 8081 as port and save.

- Now go browser on emulator, in url bar open http://burp and download certificate (For better browsing experience install Chrome)
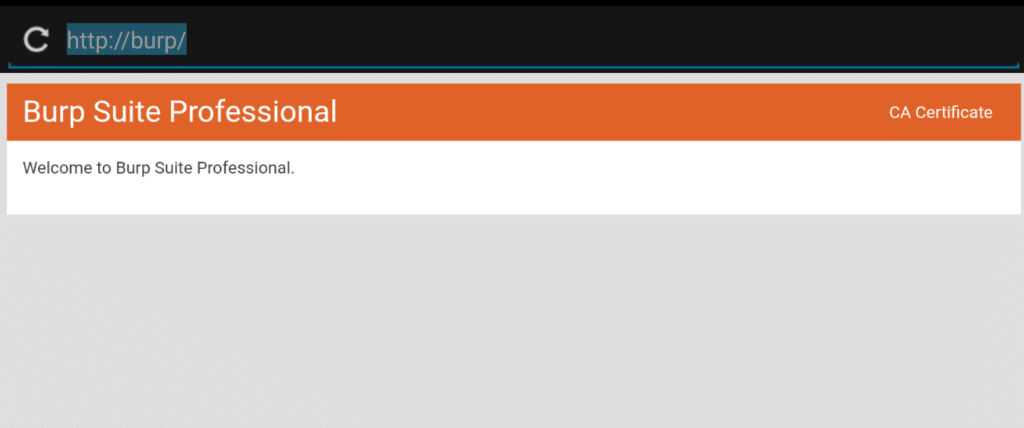
- Now go back, and click on Tools > Amaze . Give all required asked permissions. > Downloads
- Rename cacert.der file to cacert.cer

- Now go to settings and search for install certificate

- Click on Install certficates and select certficate file. Phone Model > Download > cacert.cer and click on ok. If it ask for any PIN or password setup then do it.

- Now if we open any browser, we will be able to see requests in Burp Suite

But wait. This is only for browser, we will further see about android apps.
Proxying Apps
Before we installed frida and objection. We will use these tools to help bypass ssl pinning. Before, we have to download frida-server. There are multiple frida server, but for us using android emulator we will download frida-server-15.1.17-android-x86.xz . This totally depends on Emulator and its architecture. If you want to find out, try the following command.
nox_adb.exe shell getprop ro.product.cpu.abi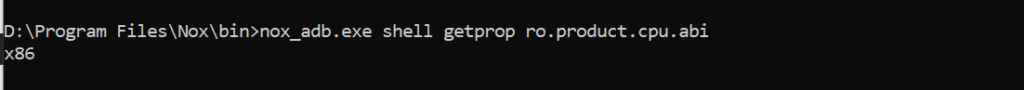
After downloading Frida server, First unzip it and move it to emulator using adb. Please make sure to use this command from Nox bin directory.
nox_adb.exe push "C:\path\to\download\folder\frida-server" /data/local/tmp/After pushing the frida-server, we need to give permissions and execute it.
nox_adb.exe shell "chmod 777 /data/local/tmp/frida-server"
nox_adb.exe shell "/data/local/tmp/frida-server &"
Now Install any apps, you want to try bypassing SSL pinning. For bypassing we will use frida scripts from frida-codeshare. Most common scripts are Universal Android SSL Pinning Bypass with Frida and frida-multiple-unpinning. Download them and save in the Nox installtion directory. It doesn’t guarantee to work in all android apps. However we can try every possible methods and see which works for which app.
SSL Pinning Bypass using Frida scripts
I will choose Coinbase apk for demonstartion purpose.
- Install the apk by dragging or install from google play store.
- View installed available apk in emulator
frida-ps -Uai
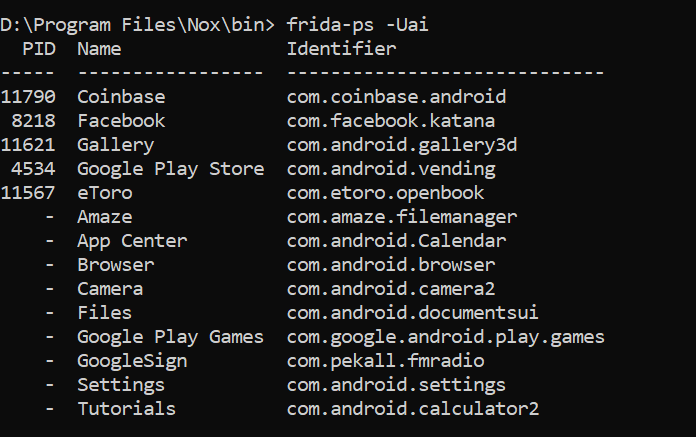
Also copy the certificate in frida-server directory and give permissions.
nox_adb.exe shell "cp /sdcard/Download/cacert.cer /data/local/tmp/cert-der.crt"
nox_adb.exe shell "chmod 777 /data/local/tmp/cert-der.crt"- Use the following command to bypass ssl pinning in Coinbase
frida -U -f com.coinbase.android -l universal-android-ssl-pinning-bypass.js --no-pause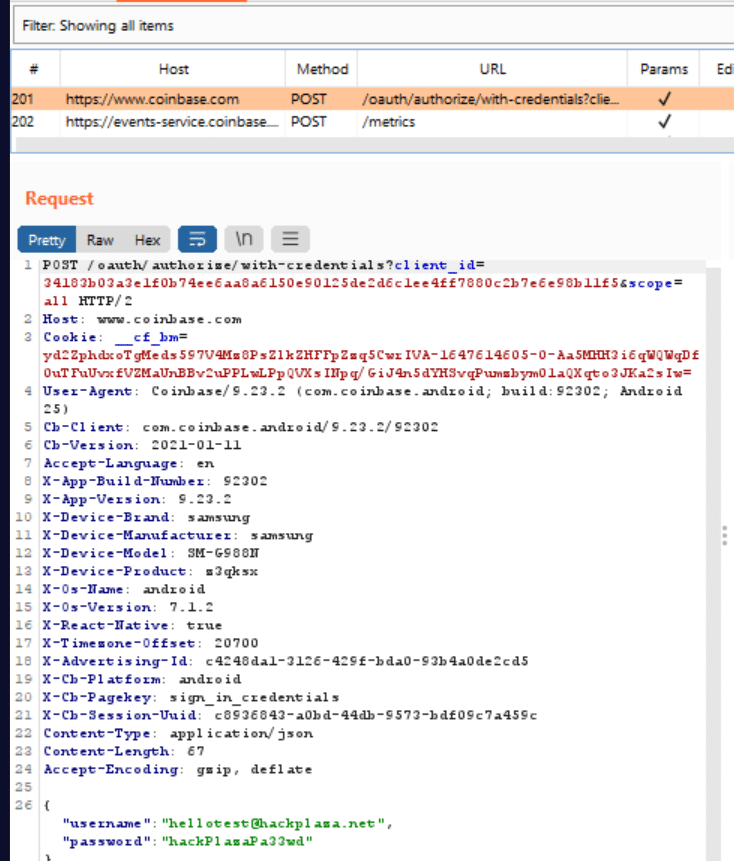
So we bypassed Coinbase SSL pinning using Universal Android SSL Pinning Bypass with Frida .
SSL Bypass using Objection
As we already installed objection during python setup. Lets get directly into bypassing SSL pinning of eSewa apk for demonstartion purpose.
- Get the identifier name using: frida-ps -Uai
- Now use the follwing command
objection -g "com.f1soft.esewa" explore
- Now to bypassing ssl pinning
android sslpinning disable

So we succesfully bypassed SSL pinning in eSewa too. You can try both methods using Frida scripts like Universal Android SSL Pinning Bypass with Frida, frida-multiple-unpinning and Objection method.
That’s all for the article for Android Hacking Setup and SSL Pinning Bypass. If you have any queries or questions please comment. I will try to answer them and help.
